Customize Policies
Customize policies to simplify your daily operations!
In daily operations, you may need to monitor new vulnerabilities, search for affected packages, conduct license checks, and set up compliance checks for various regulations. These processes can be simplified using our customizable policies.
What is a "Policy"?
In DeepAsset, a 'Policy' is a set of rules evaluated against selected software assets. It is composed of the following key parts.
- Name: name of the policy.
- Rules: what will this "Policy" examine.
- Triggers: when will this "Policy" be examined.
- Actions: When the policy is violated, what action (e.g., FAIL, INFO, PASS.) you will take.
- Target. This defines the subjects to which this policy will be applied.
Create a "Policy"
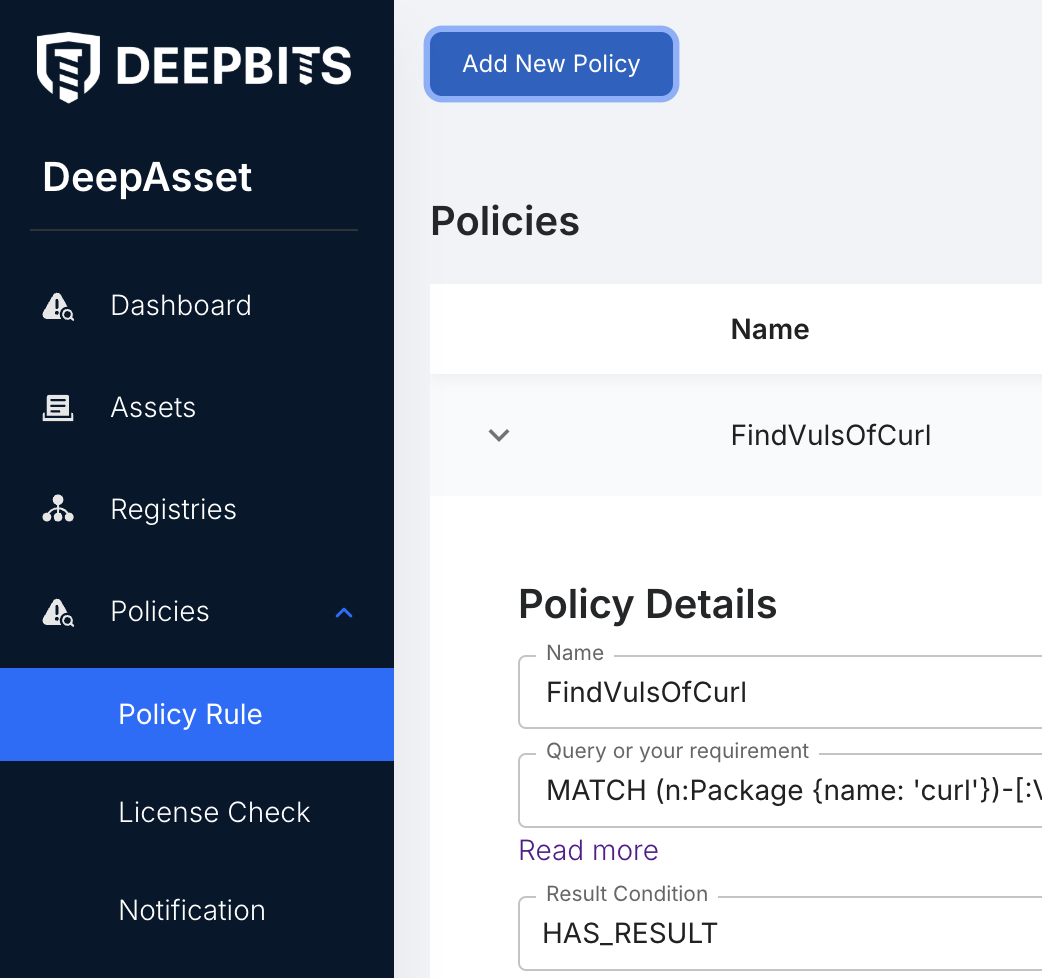
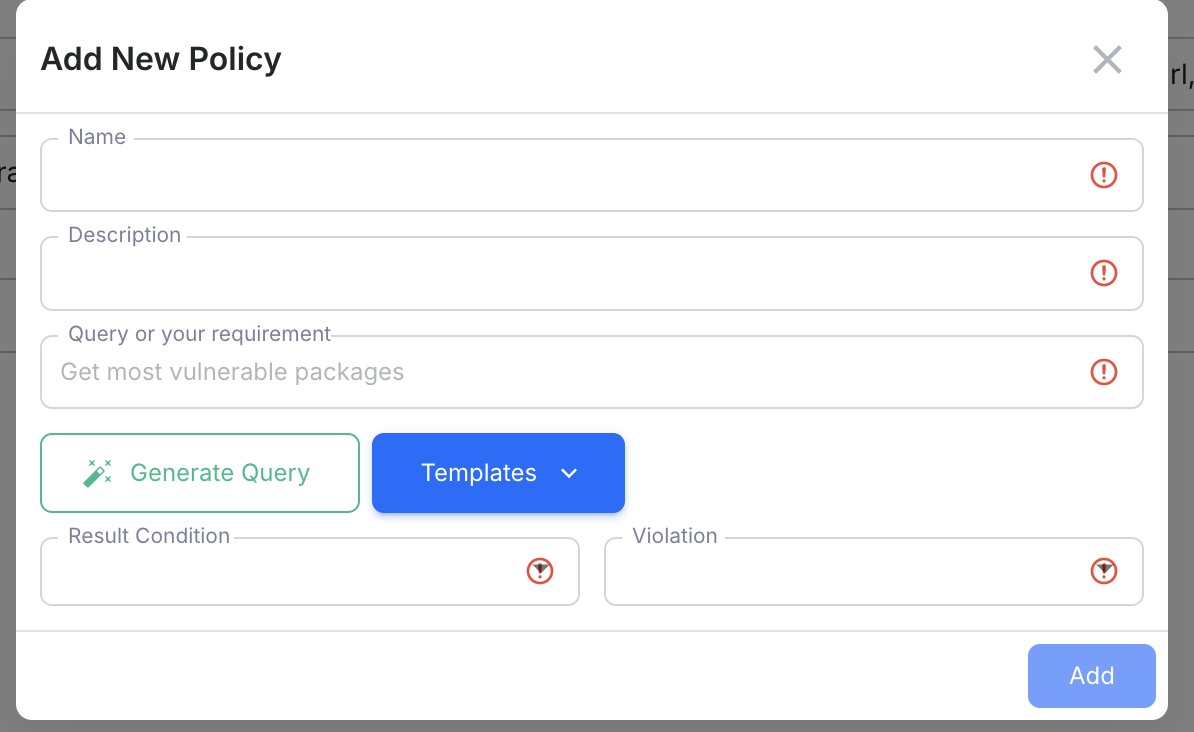
Click 'Policy Rule' in the left navigator, then click 'Add New Policy'. In the new popup window, you can add the policy information.
- Name - A helpful name to indicate what's the policy for
- Description - add details of this policy.
- Query or your requirement
- Query: It is neo4j's query language that was discussed in Write Queries
- Your requirement: DeepAsset also has a beta feature that translates your natural language into queries. Just input what you're checking, e.g., 'Find the most vulnerable packages', and click 'Generate Query'. It will automatically generate the query.
- Template: DeepAsset also provides popular query templates that can be used directly.
- Result condition - Determine if the above Cypher query with non-empty results should trigger the policy.
- Violation -If the policy matches the conditions, which violation level ('INFO', 'WARN', 'FAIL', 'PASS') do you want it to be? Different violation levels indicate different degrees of attention required.
Click "Add", the policy is created.
Select Targets of The Policy.
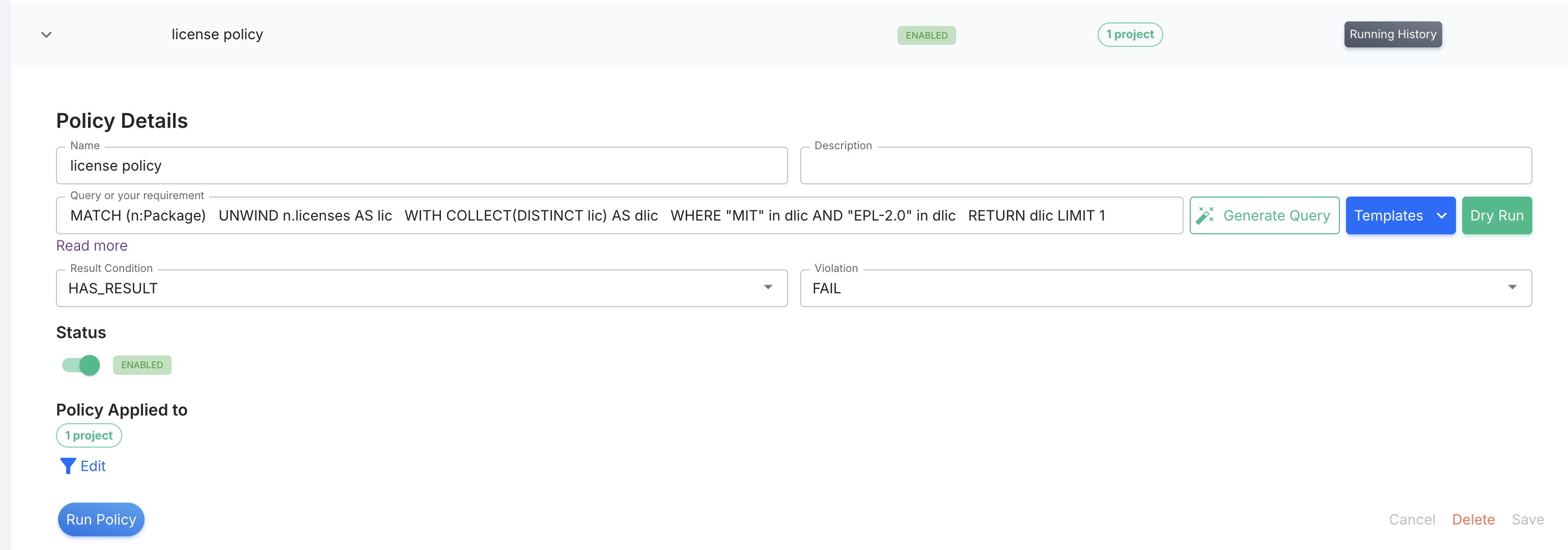
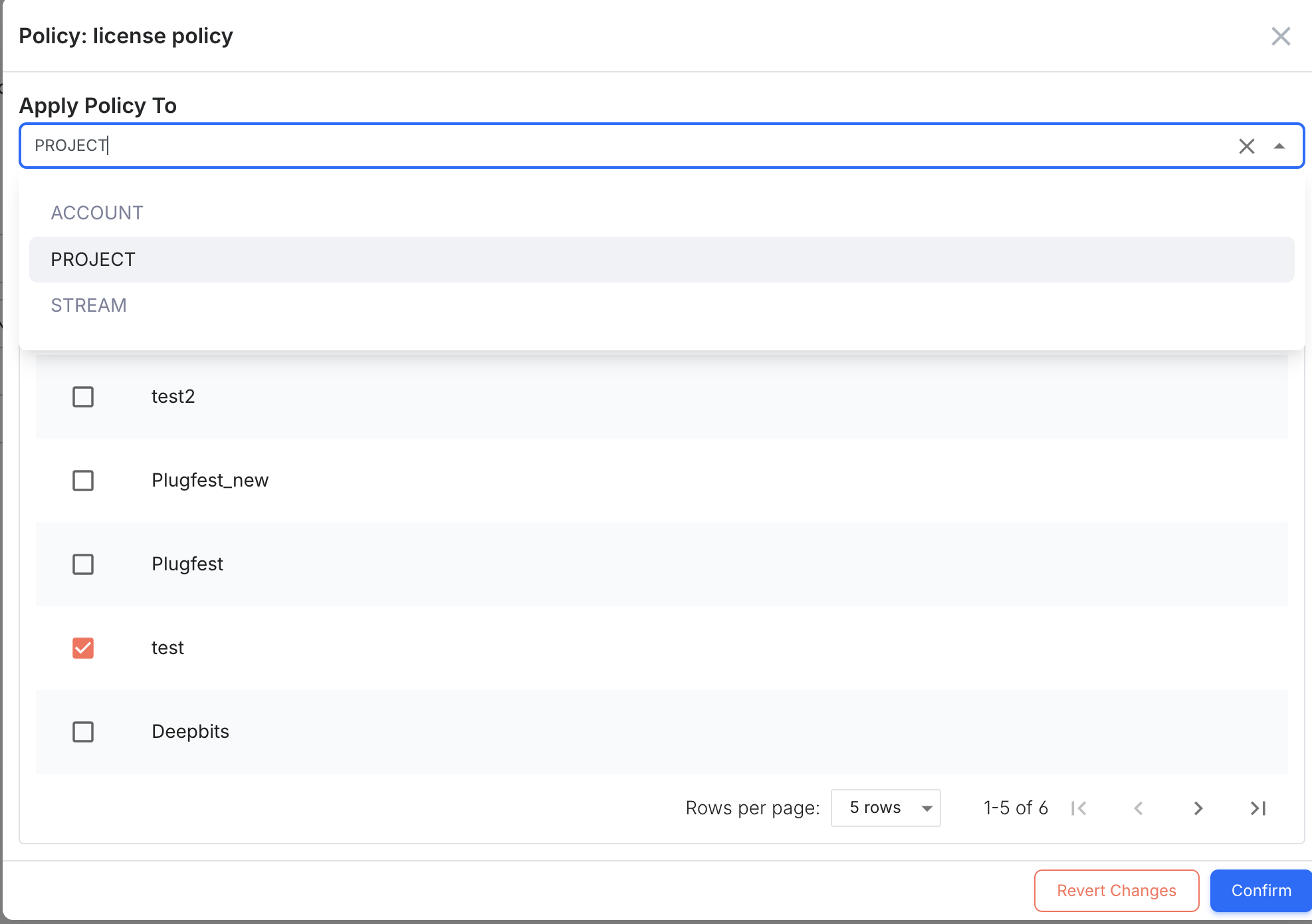
By default, a newly created policy will not apply to any resources. You need to specify which resources the policy applies to. A policy can be applied to: 1) the entire account, 2) selected projects, or 3) selected STREAMS.
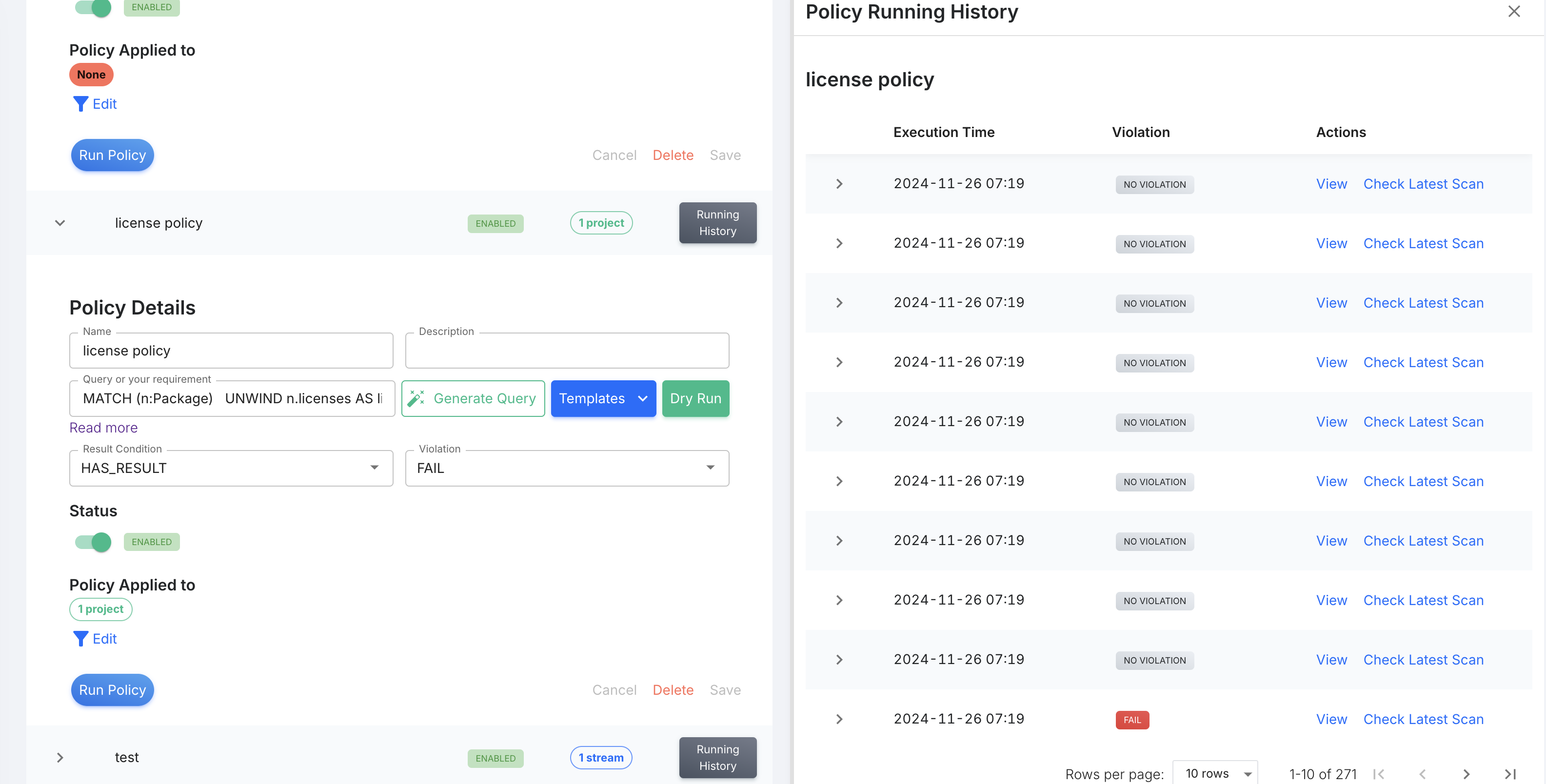
When a "Policy" is Evaluated?
A policy will be evaluated
- When policy is changed, we'll execute the policy once you modify the policy content.
- Manually trigger by clicking "Run Policy.
- A new scan of your software assets is triggered when there are changes to your software assets, updates to the vulnerability database, or when the scan is manually triggered.
Updated about 1 month ago
