DeepMalware
Malware Analysis
The malware analysis module exploits code reuse, which is very common in malware, to detect and analyze new, unknown variants. It first uses DeepDi to quickly generate the disassembly code of a malware variant, and then find similar functions to detect and identify its malware family by comparing it to other samples in our database. Our system can show where each function in a user-submitted malware sample occurs in all other malware samples in our dataset, and compare their disassembled code.
Upload or Search Samples
Users can upload new malware samples or search existing malware samples by their new, unknown variants. It first uses DeepDi to quickly generate the disassembly code of a malware variant, and then find similar functions to detect and identify its malware family by comparing it to other samples in our database. Our system can show where each function in a user-submitted malware sample occurs in all other malware samples in our dataset, and compare their disassembled code in . SHA256 value.
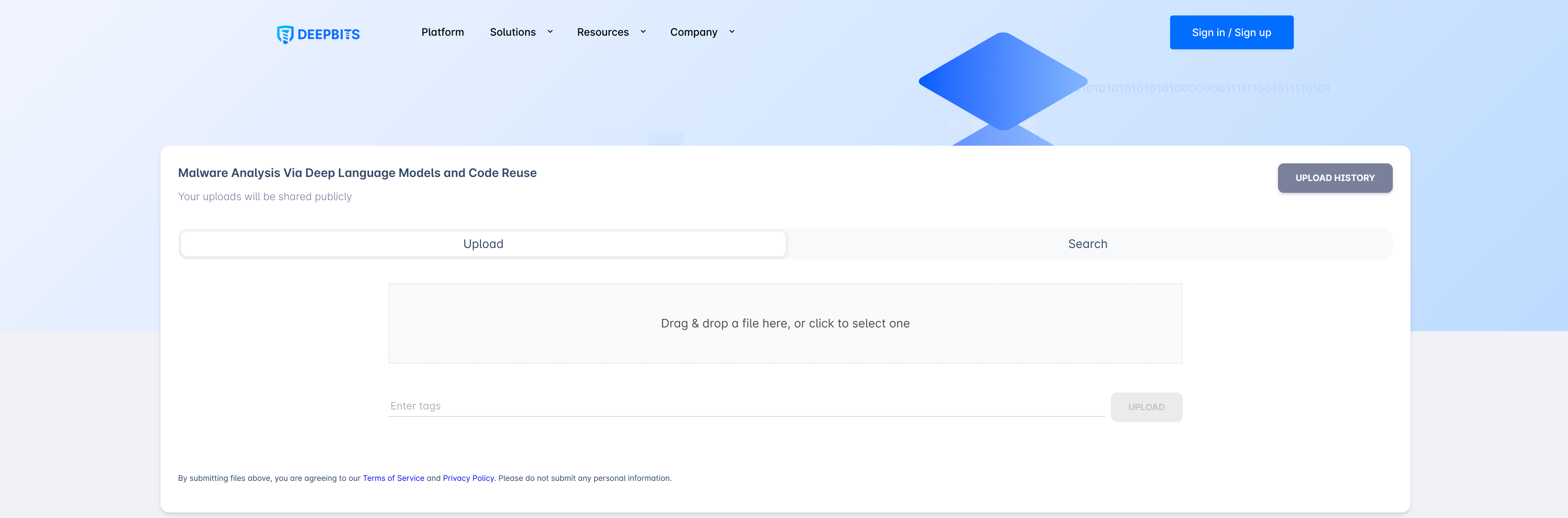
Upload or Search Malware
Statistics
The system will count weekly, monthly, and overall distribution of various malware families.
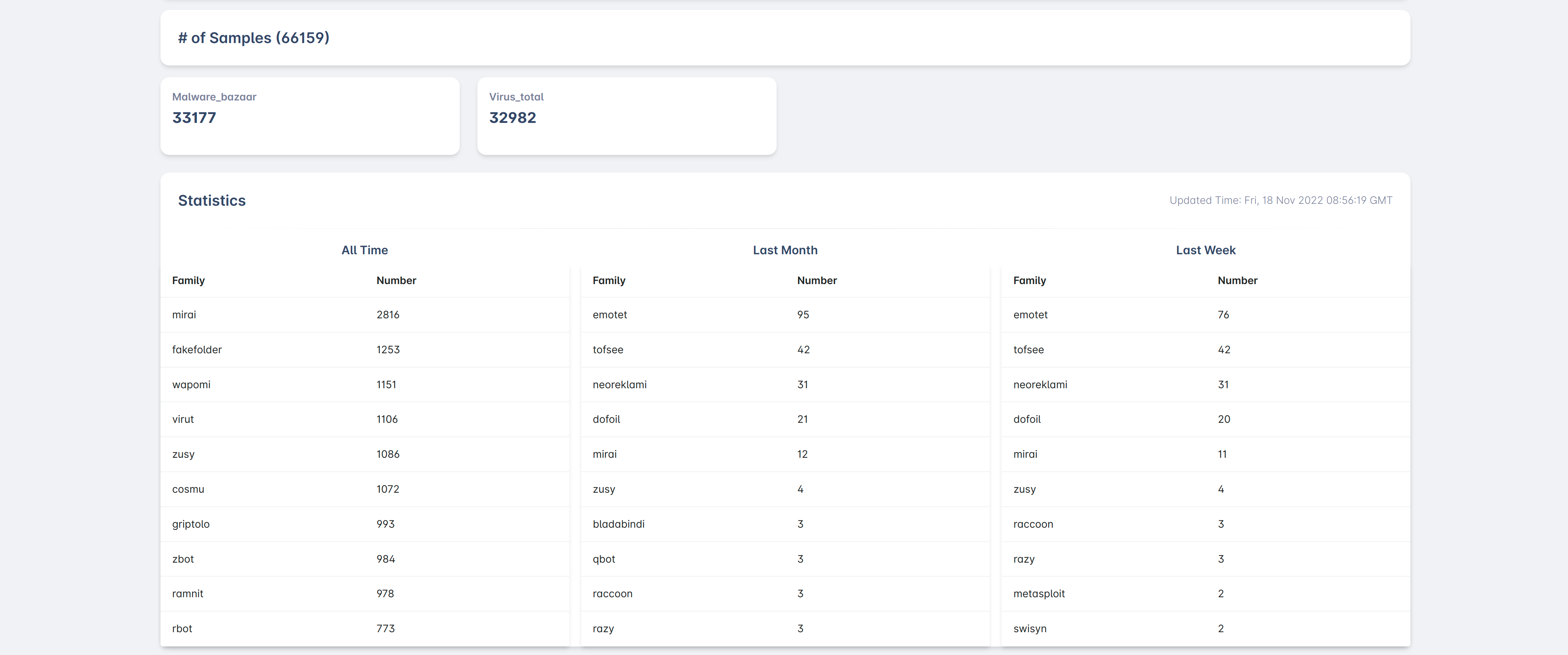
Statistics Information
Latest Samples
Information about the 50 most recently discovered malware samples.
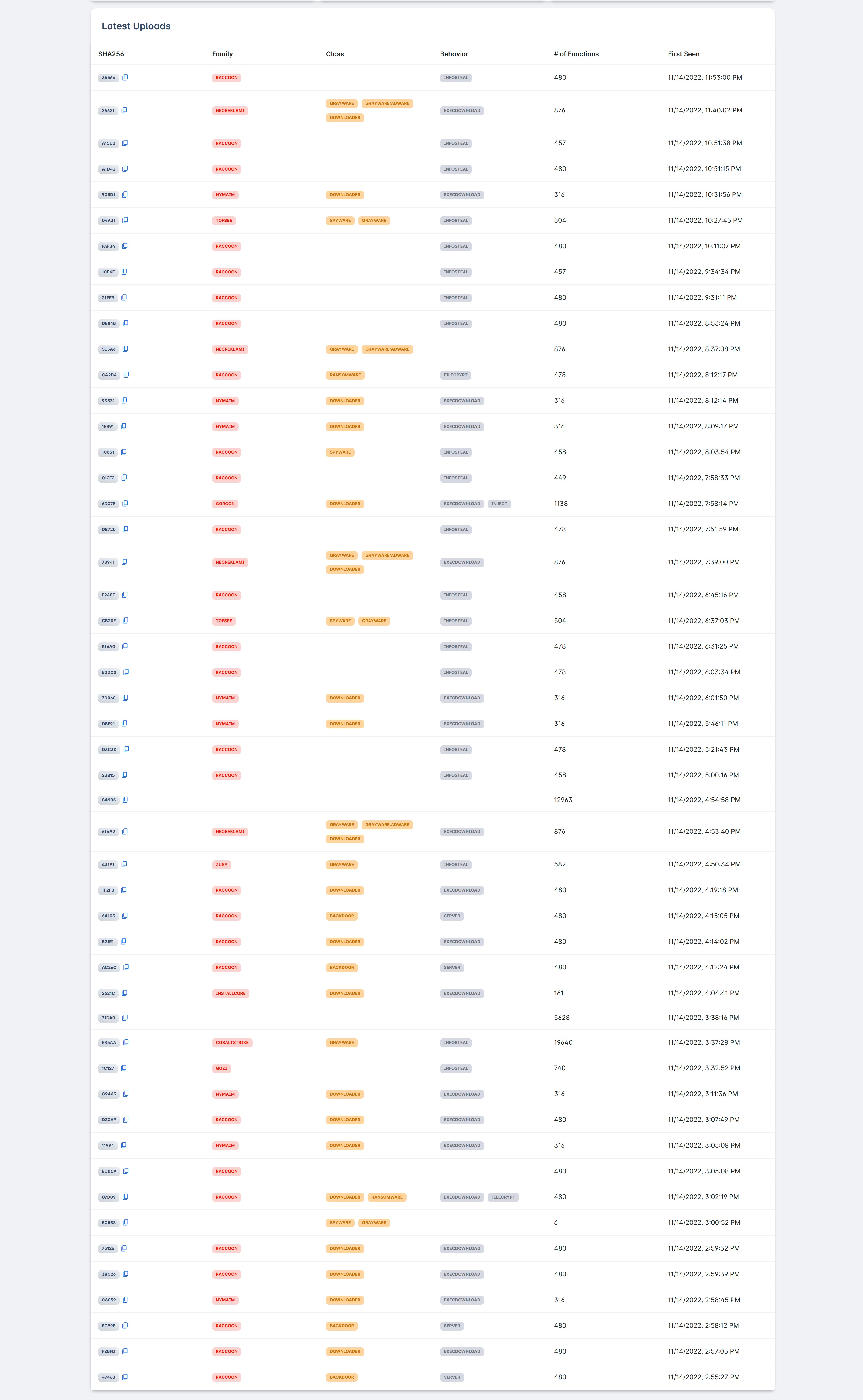
Latest Samples
Scan Results
The system will list all the functions in the submitted sample and show the number of times te new, unknown variants. It first uses DeepDi to quickly generate the disassembly code of a malware variant, and then find similar functions to detect and identify its malware family by comparing it to other samples in our database. Our system can show where each function in a user-submitted malware sample occurs in all other malware samples in our dataset, and compare their disassembled code in .hey appear in different malware families. Functions can be sorted by relevance or address.
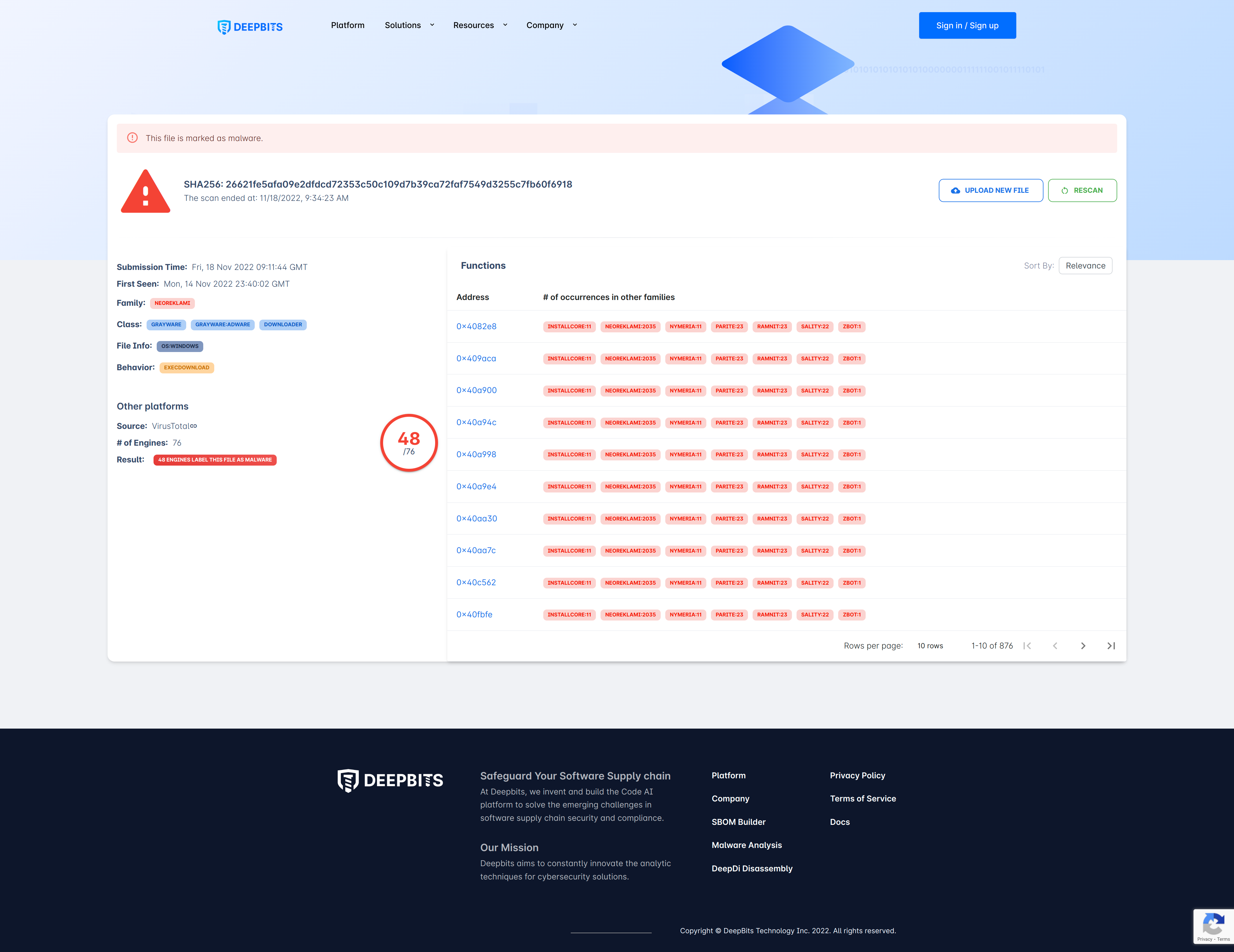
Scan Results
Function Details
After clicking the address of the function, the system will display the disassembly code of this function, and all other samples containing similar functions
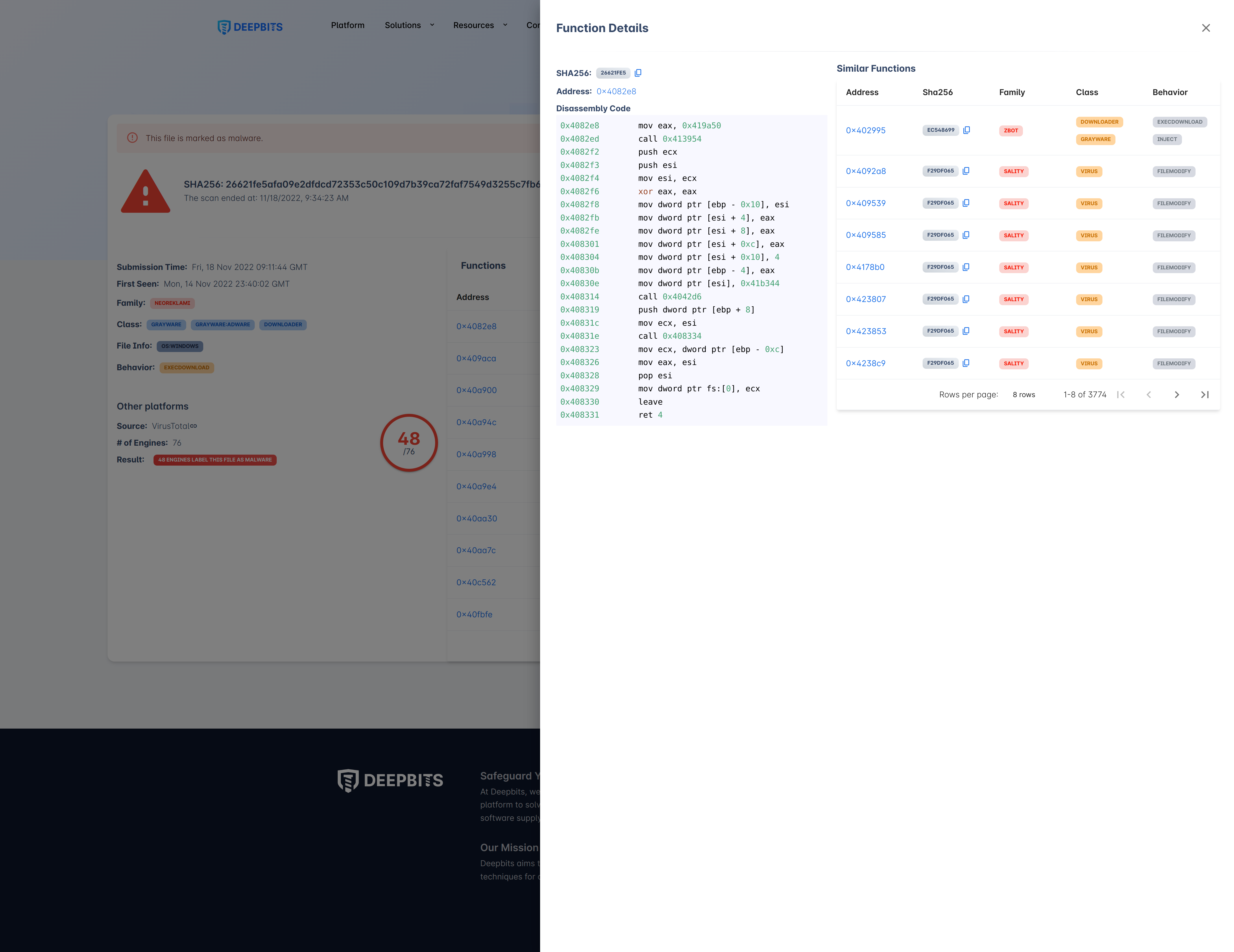
Function Details
Similar Function Comparison
After clicking the SHA256 value of the sample with similar function, the comparison between the disassembly code between these two similar functions will be displayed.
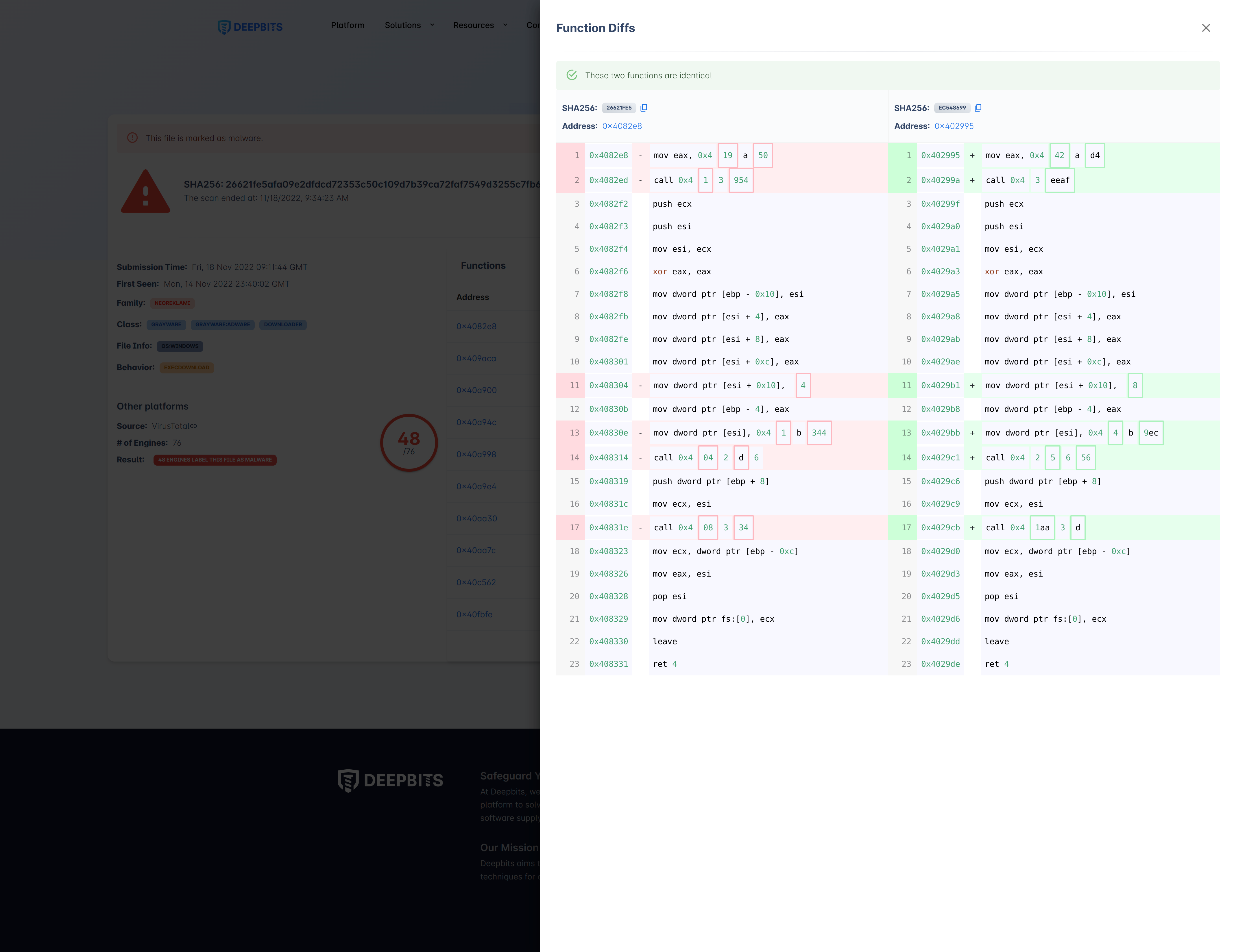
Similar Function Comparison
Updated about 1 month ago
