Link AWS ECR
Deepbits provides the capability to analyze your Docker images stored on AWS ECR. If your organization plans to use AWS ECR as your Docker container registry, integrating DeepAsset offers the most efficient and seamless solution for ensuring the security and reliability of your container images.
Setup
- Go to Integrations-AWS.
- Choose your account primary region, we'll create a cloudformation stack for your AWS account in the region you selected.
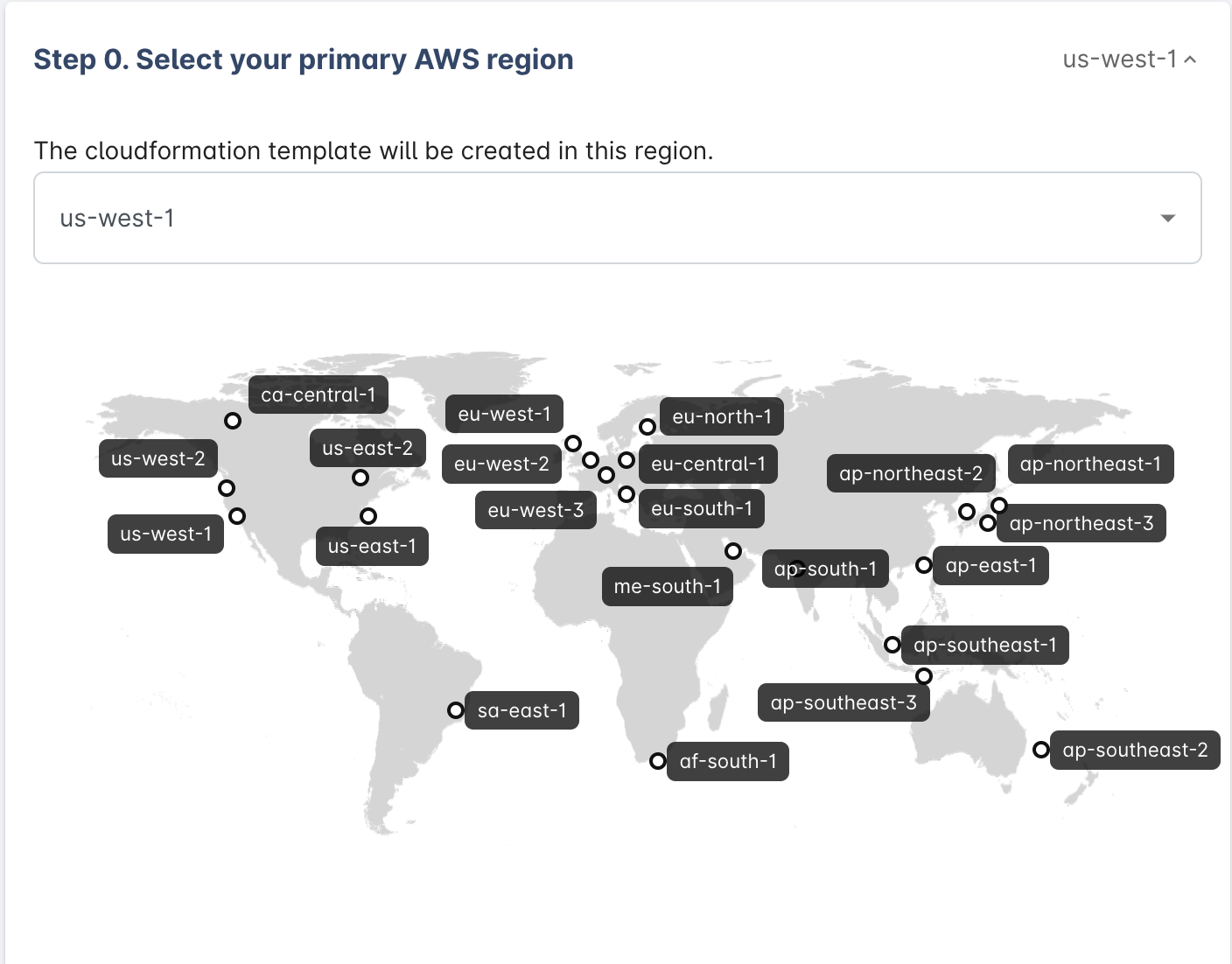
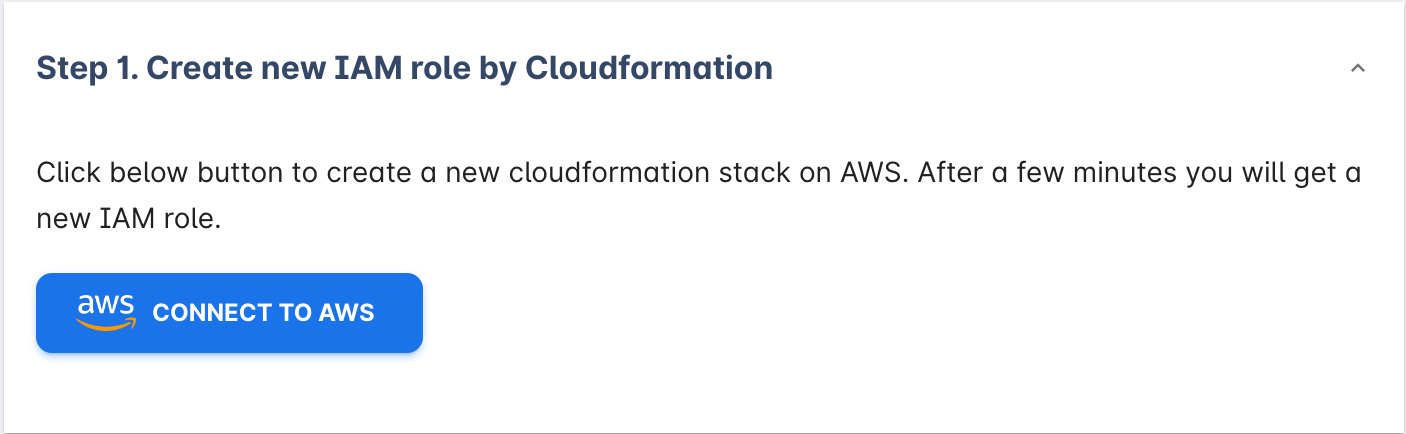
- Create the IAM role with our cloudformation template.
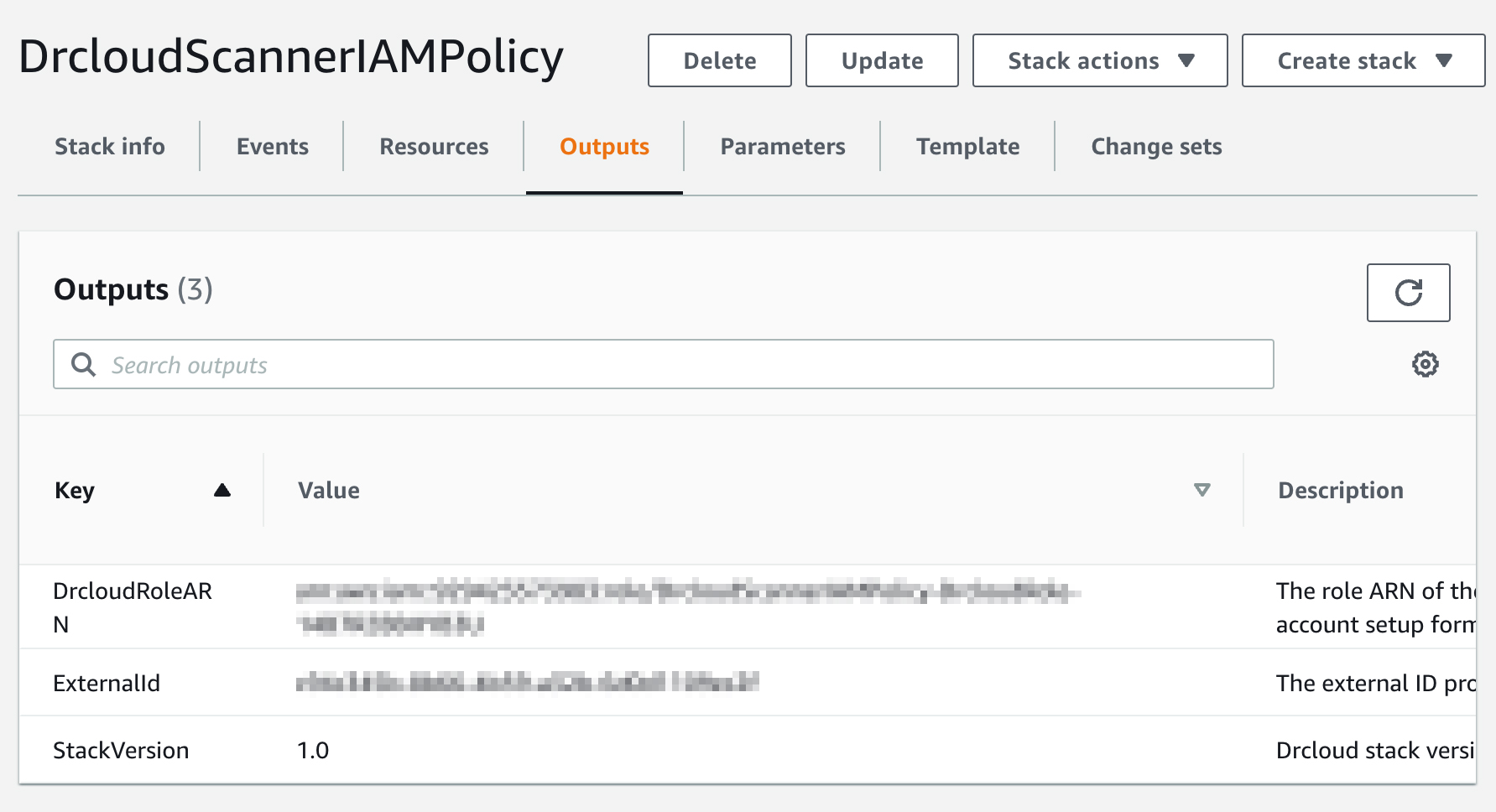
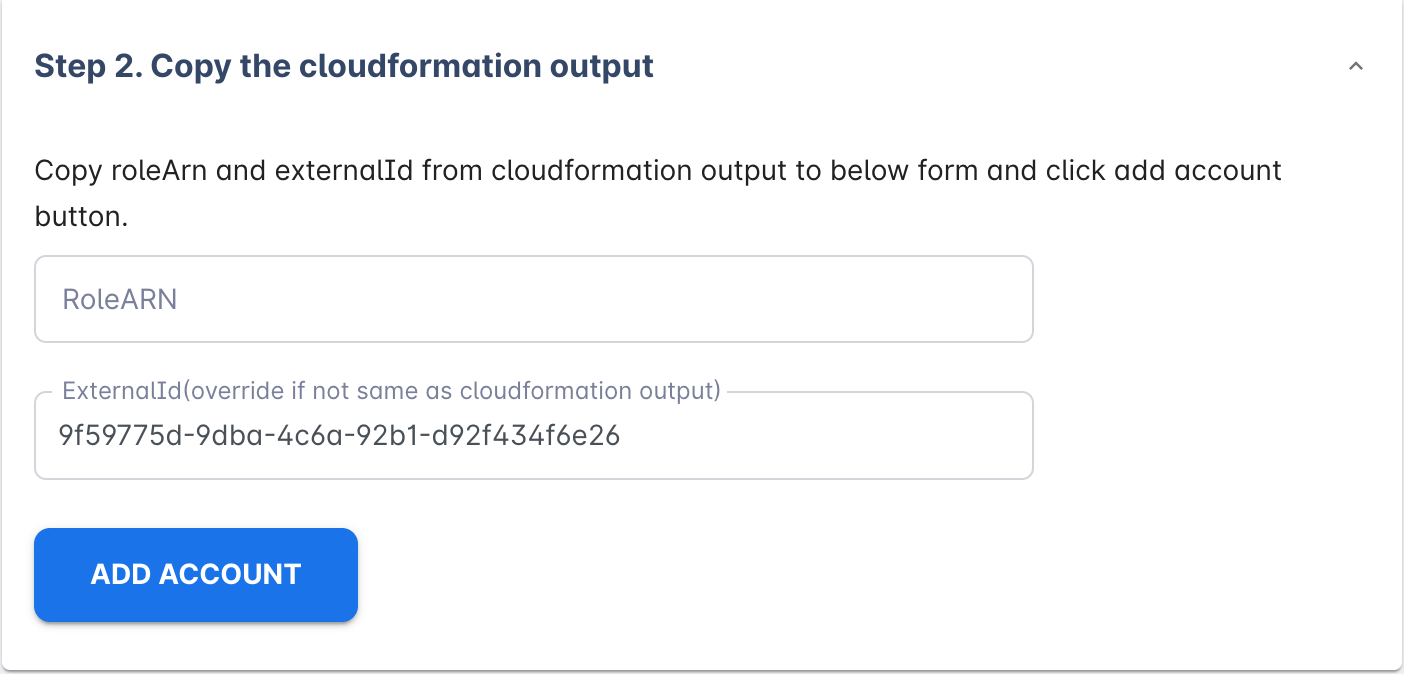
- Finish the setup by filling in RoleARN and ExternalId from the cloudformation output.
Security Concern
As an account owner, you may be concerned about how deepbits access your AWS data and store it.
Access AWS data
By creating an IAM role with our cloudformation template, you'll create an IAM role that only allows deepbits scan agent to access limited permissions. You can view the detail of the template by clicking this URL.
Trust relationship
Only these two principals can assume your AWS IAM role.
"arn:aws:iam::733851098553:role/drcloud-scanner-role",
"arn:aws:iam::733851098553:user/drcloud-scanner"733851098553 is the deepbits account id, which means only deepbits can use the IAM roles created in your AWS account.
Permissions we need
arn:aws:iam::aws:policy/SecurityAudit - monitors accounts for compliance with security requirements.
drcloud-additional-policy - read-only permissions in order to complete the watch ECR image feature.
Store AWS data
We only store necessary information like your ECR repository list and image list information in our database. Each account's data only can be visited by the account owner safely.
Data deletion
Whenever you don't want to use the deepbits AWS-related feature, you can always click ~Unlink Account~ button on AWS - Accounts page. By clicking the unlink button we'll permanently delete all your AWS account and ECR data in our database. This action can't be undone.
Updated about 1 month ago
