Manage assets via Query
One challenge in managing software assets is finding the desired software asset. Typically, users can do this using filters, such as name or license type. This works for simple cases, but scenarios like 'finding the software asset with the most vulnerabilities' are more difficult to implement. DeepAsset stores the analysis results in a graph database, enabling users to easily write query language for complex cases.
Search across all your software assets.
On the dashboard page, you will see the place to search across all your software assets. E.g., let's find the CVEs that affect most packages.
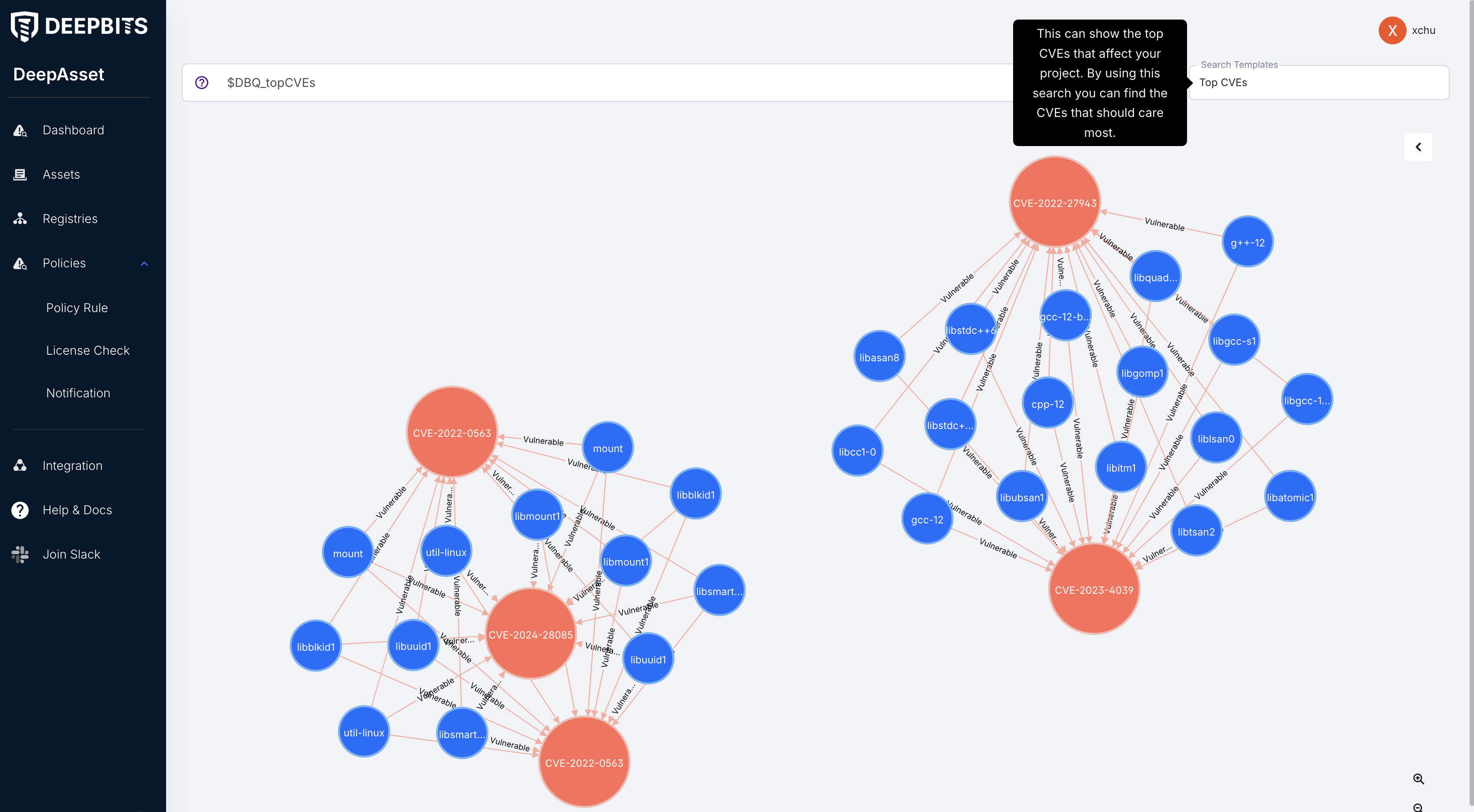
Search in a software asset
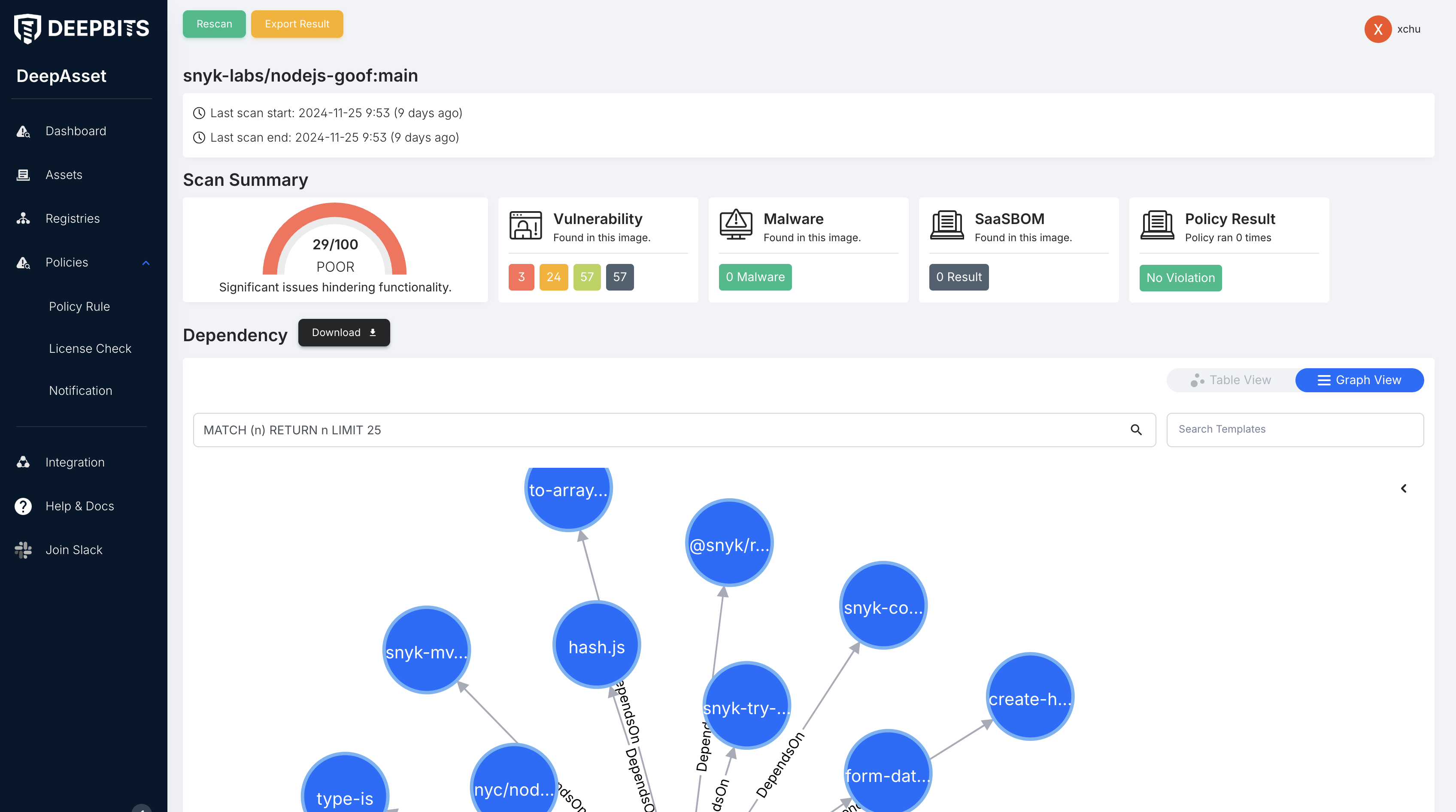
On the scan results page, you can analyze queries in your dependencies, e.g., find the packages with the most vulnerabilities.
Write queries
The above queries are implemented using the Neo4j database, leveraging Cypher query language, a powerful tool for querying and analyzing complex relationships in graph data. Here is a quick tutorial of Cypher language. On DeepAsset platform, you have two ways to write Cypher queries.
- Write cypher language manually. Just go over the tutorials of Cypher language and learn how to write them manually.
The query might look something like this:MATCH (n: Package) RETURN n LIMIT 25 - Generate cypher language from natural language. DeepAsset enables users to generate Cypher queries from natural language. For example, a query like 'find packages with CVE-2021-3711' can be converted into a Cypher query. While it may not always produce perfect results, it significantly reduces the effort required to write complex queries.
The query might look something like this:
Find packaes with CVE-2021-3711Nodes and Relations in query result
The analysis results are stored in a Neo4j graph database. Nodes and relationships represent different pieces of information from the analysis. Queries are used to identify and retrieve relevant nodes or relationships of interest.
Nodes
There are two types of Nodes.
- Package node: Could be a software package or a docker base image like Ubuntu. Below is properties of a Package Node.
{
"id": "",
"name": "the package name like curl",
"userId": "the deepbits user id",
"resourceId": "the scan result that cause this node to generate",
"projectAssetId": "the assets that this scan for, it could be a github commit or docker hub image",
"streamId": "the sbom stream for this scan result, could be a github branch or docker hub tag",
"projectId": "the deepbits project id, can include many assets",
"resourceType": "image, ecrImage, file, dockerHub, githubCommit, memoryDump, stream",
"purl": "something like: purl: pkg:g++/4:11.2.0-1ubuntu1",
"version": "the package version, sample: version: 4:11.2.0-1ubuntu1"
}- Vulnerability node: Usually it's a CVE. Below is properties of a Vulnerability Node.
{
"name": "Alpine Linux v3.11",
"purl": "os:Alpine Linux v3.11/1.1.24-r2",
"version": "1.1.24-r2",
"userId": "your user id",
"userId": "the deepbits user id",
"resourceId": "the scan result that cause this node to generate",
"projectAssetId": "the assets that this scan for, it could be a github commit or docker hub image",
"streamId": "the sbom stream for this scan result, could be a github branch or docker hub tag",
"projectId": "the deepbits project id, can include many assets",
"resourceType": "image, ecrImage, file, dockerHub, githubCommit, memoryDump, stream",
}Relations
DependsOn: If a Package Node A depends on a Package Node B, it means Package A uses Package B (e.g., Alpine Linux v3.11 depends on BusyBox).
Vulnerable if a Package Node B depends on a Vulnerability Node, it means that Package B is affected by that vulnerability (e.g., BusyBox is vulnerable to CVE-2021-42384)."
You can use those node and relations in cypher query to query the result you want.
Interpreting the query results
The query results are displayed as nodes in a graph, where each node represents a software package that matches the query. Users can explore the graph further by clicking on nodes to view detailed information about each component and its dependencies. Additionally, users can click the 'From Image' link to navigate to the source resource, such as a Docker image, GitHub repository, or file.
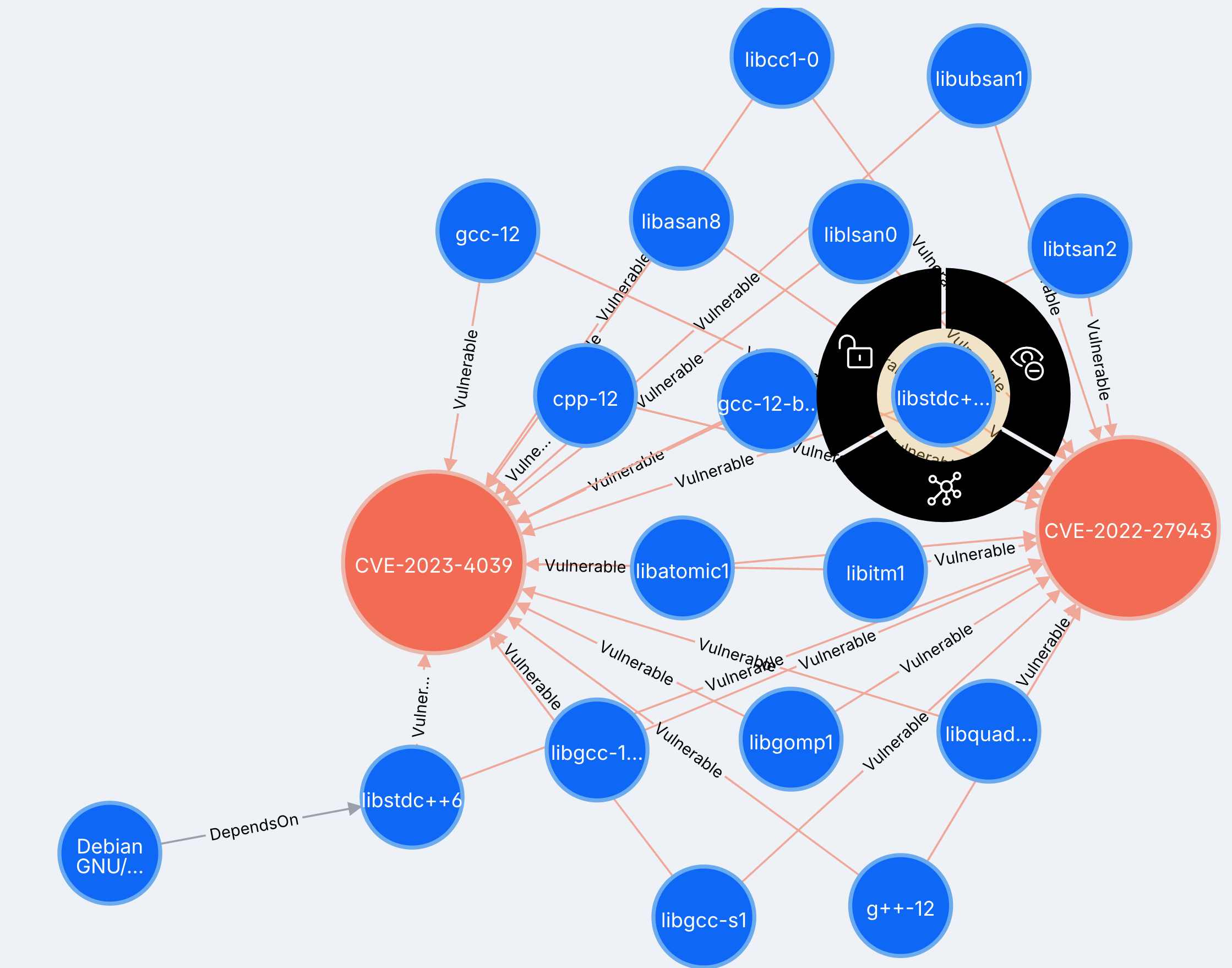
Query Examples & Templates
Examples
Query packages that have relationship with specific package
MATCH (n)-[]-(x) WHERE n.name = "Alpine Linux v3.11" RETURN n, x LIMIT 25Query packages affected by specific CVE
MATCH (n)-[]-(x: Vulnerability) WHERE n.name = "vim" RETURN n, x LIMIT 25You can find more at our "Useful cypher queries" docs.
Query templates
DeepAssets offers a selection of frequently used query templates. Users can simply click on a template and make minor modifications to tailor it to their needs. Below are a list of query templates.
- Find all vulnerabilities associated with a specific package
MATCH (n:Package {name: 'curl'})-[:Vulnerable]->(v:Vulnerability) RETURN v;- List all packages in a specific user's project with their associated vulnerabilities
MATCH (n:Package {projectId: 'YOUR PROJECT ID'})-[:Vulnerable]->(v:Vulnerability)
RETURN n,v- Retrieve the top 10 vulnerabilities affecting the highest number of packages
MATCH (v:Vulnerability)<-[:Vulnerable]-(n:Package) WITH v, count(n) as AffectedPackages ORDER BY AffectedPackages DESC LIMIT 10 RETURN v;- Get a list of all vulnerabilities for a specific resource type like Docker images
MATCH (n:Package {resourceType:'dockerHub'})-[:Vulnerable]->(v:Vulnerability) RETURN v;- Return packages with no known vulnerabilities
MATCH (n:Package) WHERE NOT (n)-[:Vulnerable]->() RETURN n LIMIT 20;
- Find vulnerabilities introduced in a specific SBOM stream
MATCH (n:Package {streamId: 'your stream id'})-[:Vulnerable]->(v:Vulnerability) RETURN v;
- Identify which package are affected by a specific vulnerability
MATCH (n:Package)-[:Vulnerable]->(v:Vulnerability {id: 'CVE-2018-1107'})
RETURN nmore to come...
Updated about 1 month ago
